CMMC v2.0 Launched...Well, Sort Of
As many readers of the cyberTAP blog already know, suppliers of goods and services to the United States Department of Defense (DoD) have been put on notice to improve their cybersecurity postures. This process started in November 2017 when the Defense Federal Acquisition Regulation Supplement 252.204-7012, commonly referred to as DFARS 7012 was released. DFARS are formal regulations regarding how business is conducted with the DoD. DFARS 7012 called for government contractors in the Defense Industrial Base to properly protect Controlled Unclassified Information (CUI). These requirements were placed into purchasing contracts and required that companies self-attest to have fully implemented the following items in their organizational cybersecurity programs:
- Implement all 110 controls of the NIST SP800-171r1 (at the time, now r2).
- Create and manage a System Security Plan (SSP) and Plan of Action and Milestones (PoAM) for systems accessing, transmitting, processing, or storing CUI.
- Develop an incident response capability and report security incidents involving CUI to the DoD within 72 hours of detection.
By September 2019 it was clear to DoD that although companies had self-attested to being compliant with DFARS 7012 requirements, very few had done anything to improve their cybersecurity posture. In fact, many organizations’ cybersecurity programs were leaps and bounds away from being compliant. It was also apparent that not all companies needed the level of cybersecurity sophistication that NIST SP800-171r2 required. Thus, the cybersecurity maturity model certification (CMMC) was developed. The idea behind CMMC was to right-size the maturity of the cybersecurity program commensurate with the sensitivity of data shared, utilized, accessed, or created to fulfill a DoD contract. CMMC had five levels of maturity, with certifications only being issued for maturity levels 1, 3, and 5. The required CMMC controls were sourced from NIST 800-171 and the larger NIST SP800-53 security control catalog. CMMC required an assessment to be performed by an external party, self-attestation at any level would not be possible. Maturity level 1 organizations would need to implement 17 controls to protect Federal Contract Information, this is material that is not meant to be public but does not jeopardize the security or safety of a defense system or the war fighter if it were improperly released. Level 3 and 5 organizations would possess or create Controlled Unclassified Information (CUI) in addition to FCI. CUI requires additional protective measures to be implemented. Maturity level 3 organizations would need to implement 130 controls: 110 from NIST SP800-171 and 20 additional controls from NIST SP800-53 security control catalog. Maturity level 5 organizations would need to implement 171 controls: 110 from NIST SP800-171 and the remaining from NIST SP800-53 and NIST SP800-172.
Since CMMC had a staged 5-year rollout, it spurred the release of two additional DFARS clauses to be added to new contracts to move organizations along in their journey of securing FCI and CUI. DFARS 7019 and 7020. DFARS 7019 required that all DoD contractors that are required to self-attest to complying with NIST SP800-171r2 had to compute an assessment score based on their current implementation of the NIST controls. This score had to be inputted into the Supplier Performance Risk Systems, commonly referred to as SPRS. A perfect SPRS score would be 110, indicating that the supplier is fully compliant with the 110 NIST controls. Not all controls are scored equally and suppliers have to calculate their score using the DoD NIST SP800-171 Assessment Methodology. Organizations without an SPRS score in the system would not be allowed to bid on any new contracts as of December 1, 2020. DFARS 7020 gave DoD the rights to come onsite and inspect systems and networks to support the investigation of a reported incident.
Due to federal rulemaking requirements, when CMMC was announced, there was a public comment period where industry provided feedback on the plan. There was an overwhelming response to CMMC, and the DoD decided to conduct a formal review of the program that had essentially been developed almost entirely by the not-for-profit CMMC Accreditation Body. The certification costs to small organizations, additional flow-down requirements from primes, and the sustainability of the CMMC auditing ecosystems were just a few major threads of concerns that were shared by DoD suppliers during the comment period.
The community has been anxiously anticipating the release of the DoD review of the CMMC program since March 2021. Many had hopes that the CMMC would get abolished, and it would be business as usual for DoD suppliers. That’s not the case. The review was released on November 3, 2021.
So, are the major changes in CMMC v2.0?
It’s almost like we are back at the beginning with DFARS 7012, but not exactly.
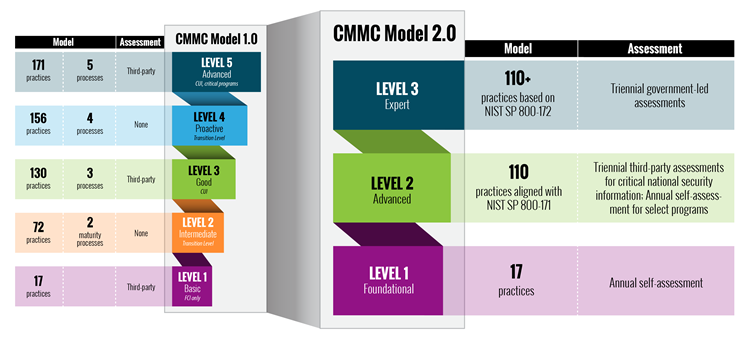
The transitional levels 2 and 4 have been completely removed from the model. Makes sense since no certifications were ever planned or these levels.
Maturity level 1 will still require 17 controls, these controls are still believed to provide foundational cybersecurity protections. A big change for level 1 organizations is that an annual self-attestation of compliance is all that will be required. In addition, gaps will be allowed to be managed via a Plan of Action and Milestones process for 180 days. The highest-weighted requirements will not be permitted to be on a PoAM. Did anybody say…”What’s our priority?”. The DoD will be establishing a minimum score that still permits certification when a PoAM is used to manage control gaps.
All maturity processes from CMMC v1.0 have been dropped. That means that maturity level 2 organizations (formerly level 3) only need to be compliant with the 110 controls (rather than the 130 in CMMC v1.0) found in NIST SP800-171r2 (so essentially exactly what they are supposed to be doing today…). For certain types of suppliers, self-attestation might be allowed. Whereas other organizations will be required to have an assessment conducted by an external CMMC certified professional auditor. This requirement will be indicated on a contract-by-contract basis.
Maturity level 3 organizations (formally level 5) will have to implement ≤ 145 controls: 110 from NIST SP800-171r2 and up to 35 from NIST SP800-172. Level 3 certifications will require a government-led assessment every three years.
The staged rollout plan for contracts requiring a CMMC certification is tentatively on hold. Why? The formal rulemaking process to finalize the DFARS interim rules (DFARS 7019, 7020, and 7021) is believed to take 9-24 months. No CMMC requirements will be inserted into contacts until the rules have been published in the federal register. So rather than all contracts having a CMMC requirement by 2025, it will likely be closer to 2027.
This delay in certification requirements should not be considered a time to take a breather, but it should be considered an opportunity to properly architect your environment so that CUI can be properly protected. If you are serving the DoD in a way that includes creating or handling CUI, you are currently obligated to implement NIST SP800-171r2 controls. This was and is still your current priority.




