Articles
-
Haunted Networks & Ghosts in Machines: Cybersecurity’s Spooky Side
Hope Trampski - Oct. 31, 2025
Even when we think that viruses are gone, worms have been eliminated, and cybercriminals taken care of, traces can still linger. Just because we can’t see them, doesn’t mean they are gone for goo… Read More
-
Quick Guide: Cybersecurity for College Students
Hope Trampski - Oct. 30, 2025
Continuing with our quick guide series, today we’ll be going through some smart habits and safety tips for current college students. While this is aimed at college students living and working on … Read More
-
Quick Guide: Cybersecurity for Teens
Hope Trampski - Oct. 21, 2025
Today's teens are more connected to the digital world than ever before. They aren’t just on social media; they’re online gaming, shopping, and messaging. Even if your teen isn’t on social media, … Read More
-
Quick Guide: Cybersecurity for Execs
Hope Trampski - Oct. 14, 2025
Executives today take on a lot. They spearhead their organization and often lead their industry on a massive scale. Unfortunately, this makes them primary targets for cybercriminals. Essentially,… Read More
-
Quick Guide: Cybersecurity For Seniors
Hope Trampski - Oct. 07, 2025
Cybersecurity matters at every age. Older generations are currently facing a multitude of challenges in this new age of technology. The adjustments that they need to make to participate in an onl… Read More
-
Quick Guide: Cybersecurity for Kids
Hope Trampski - Oct. 01, 2025
Kids today are born into a fully digital world; they won’t know a life without the modern-day conveniences of technology. From tablets, to TV, to phones, kids have access to just about anything y… Read More
-
Purdue cyberTAP Awarded Nearly $250,000 by the Center for Internet Security.
Eric Engle - Jun. 25, 2025
West Lafayette, IN – Purdue University’s Cyber Technical Assistance Program (cyberTAP) is honored to announce that we have been selected as the 2025 recipient of the Alan Paller Laureate Program … Read More
-
The Business Impact of a Breach: What Every Exec Needs to Know Before the Headlines Hit
Hope Trampski - May. 13, 2025
It's not if, but when. Data breaches happen daily, and the reality is that one might be closer to your organization than you may think. Every executive should be taking the proper steps to prepar… Read More
-
Newest HIPAA Rules
Hope Trampski - Apr. 24, 2025
What is HIPAA & What Does it Have to do with Me? Before we take a look at the new proposed HIPAA rules, let's cover what HIPAA actually is. The well-known acronym stands for Health Insurance… Read More
-
What Do You Mean New CMMC Updates?
Hope Trampski - Apr. 10, 2025
Prior to the beginning of this year the Department of Defense released a new set of Cybersecurity Maturity Model Certification (CMMC) guidelines. So, what is the CMMC? The CMMC program is a wa… Read More
-
Women in Cyber Today
Hope Trampski - Mar. 27, 2025
Thanks to the accomplishments of the pioneers before them, today’s women in cybersecurity are making leaps and bounds toward a more secure future. Let’s take a look at some of the most influentia… Read More
-
Women in Cyber: The 80s Era
Hope Trampski - Mar. 13, 2025
Today’s focus will be on the 80s era of computer science, a pivotal time for our field. The decade seemed to bring discoveries daily with the blossoming internet and the development of new progra… Read More
-
Women In Cyber: The NASA Years
Hope Trampski - Mar. 12, 2025
NASA is known as one of the greatest pioneers in the pursuit of knowledge in our modern era. Over and over, we hear about their success in the exploration of space and their advancements in the f… Read More
-
Women In Cyber: The Beginnings
Hope Trampski - Mar. 04, 2025
Ada Lovelace Ada Lovelace was a mathematician and writer in the early 1800s, best known for her work on the Analytical Engine. During her career she worked with Charles Babbage, who developed t… Read More
-
Hacktivism: Scambaiting
Hope Trampski - Jan. 12, 2025
To close out our series on hacktivism, we delve into the world of scambaiting, an online practice where internet vigilantes attempt to turn the tables on hackers and protect potential victims. Th… Read More
-
Hacktivism: Anonymous
Hope Trampski - Dec. 19, 2024
Origin The hacktivist group Anonymous was founded in 2003 on an imageboard, 4chan, which was a forum where users could anonymously post images and discussions. The name Anonymous originated from… Read More
-
Hacktivism: DarkSide Hacking Group
Hope Trampski - Dec. 12, 2024
DarkSide is a hacking group believed to be based out of Russia. They provide ransomware as a service accompanying their frequent high-profile attacks. First spotted in 2020, the group is fairly … Read More
-
Hacktivism: The Short Life of LulzSec
Hope Trampski - Dec. 05, 2024
Origins LulzSec came onto the scene in 2011 after their first recorded hack against Fox.com's website. ‘Lulz’ stands for laughs while ‘sec’ is shorthand for security essentially meaning every ti… Read More
-
Hacktivism: WikiLeaks
Hope Trampski - Nov. 28, 2024
WikiLeaks is a nonprofit media organization founded in 2006 by Julian Assange, Kristinn Hrdnsson, and Danial Mathews. The site is used to publish leaked documents from governments, corporations, … Read More
-
Hacktivism: The Chaos Computer Club
Hope Trampski - Nov. 21, 2024
Hacktivism: The Chaos Computer Club The Chaos Computer Club, founded in 1981, is Europe’s largest association of hackers. As an organization they stand for ‘freedom of information’ and aim to p… Read More
-
Hacktivism: The Cult of the Dead Cow
Hope Trampski - Nov. 14, 2024
What is the Cult of the Dead Cow? The Cult of the Dead Cow, founded in 1984, started as a group of like-minded hackers looking to improve their skills. As the group developed, they pivoted towar… Read More
-
What is Hacktivism?
Hope Trampski - Nov. 07, 2024
The term hacktivism has been a bit of a buzz word for the past couple of decades, falling in and out of popularity in accordance with the number of politically motivated hacks that grab media att… Read More
-
The Ashley Madison Hack
Hope Trampski - Nov. 01, 2024
Hacking almost always results in the release of personal information. Whether that be credit card numbers, social security numbers, or other sensitive data, leaks happen all the time. In the case… Read More
-
AI As A Tool
Hope Trampski - Oct. 28, 2024
What AI Looks Like Day to Day AI is an ever-evolving field, it seems that every day there is something new in the works. The topic of AI can get pretty complicated pretty quickly. So, realistica… Read More
-
The Dennis Kucinich CBS News Hack
Hope Trampski - Oct. 25, 2024
Hacking, in most cases, is a very selfish act. Most hackers are in it for the money or the information they can turn into money. But in some cases, hackers commit cybercrime because they believe … Read More
-
How Not to Take the Bait When it Comes to Phishing
Hope Trampski - Oct. 21, 2024
Phishing is one of the most common forms of cybercrime, with around 3.4 billion phishing emails sent each day it is nearly impossible to avoid. The good news is that falling victim to these scams… Read More
-
The Triton Malware Attack
Hope Trampski - Oct. 18, 2024
Completely unsolved cybercrime cases are relatively rare. Normally when an attack ensues, one of the most important proceedings is to trace it back to the attacker. This is especially important w… Read More
-
Why Are Software Updates So Important?
Hope Trampski - Oct. 14, 2024
The importance of keeping your software up to date cannot be stressed enough. Often, we find ourselves putting off these updates because it can be inconvenient to be without our devices for the p… Read More
-
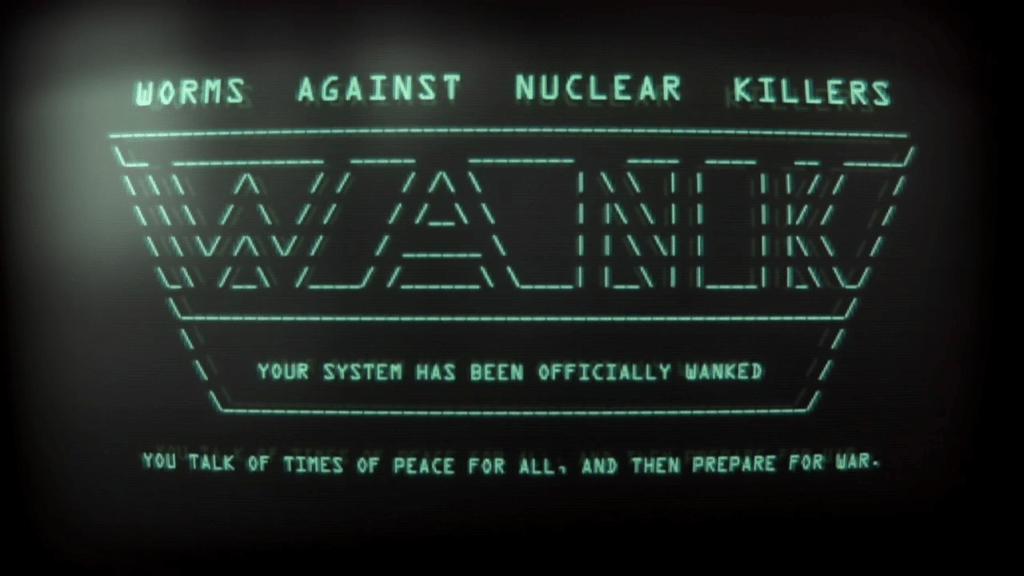
The Mystery of the WANK Worm
Hope Trampski - Oct. 11, 2024
In 1989, Galileo, a nuclear-powered spacecraft created by NASA, was set to launch. Its existence was controversial having been announced in the wake of the Challenger Disaster, but that wasn’t th… Read More
-
Multi-Factor Authentication
Hope Trampski - Oct. 07, 2024
To expand on our discussion about secure passwords from last week, let’s look at multi-factor authentication. Multifactor has only been around for about twenty years, but that's a good chunk of t… Read More
-
Broadcasting Masks and Mayhem
Hope Trampski - Oct. 04, 2024
Welcome to spooky season, we are so glad you could join us for our October series on unsolved cybercrimes! While it might be comforting to think we know the origin of every instance of malicious … Read More
-
Password Security and Password Managers
Hope Trampski - Oct. 02, 2024
Ensuring proper password safety is a never-ending task, mostly because the rules seem to keep changing. The rules used to seem easy; create a password you’ll remember. Oh wait, that’s too easy, t… Read More
-
Where are we now?
Hope Trampski - Sep. 17, 2024
Even after decades of development in our field, one thing stays consistent, change. There are always new threats, new vulnerabilities, new fixes. The only thing that stays the same is that things… Read More
-
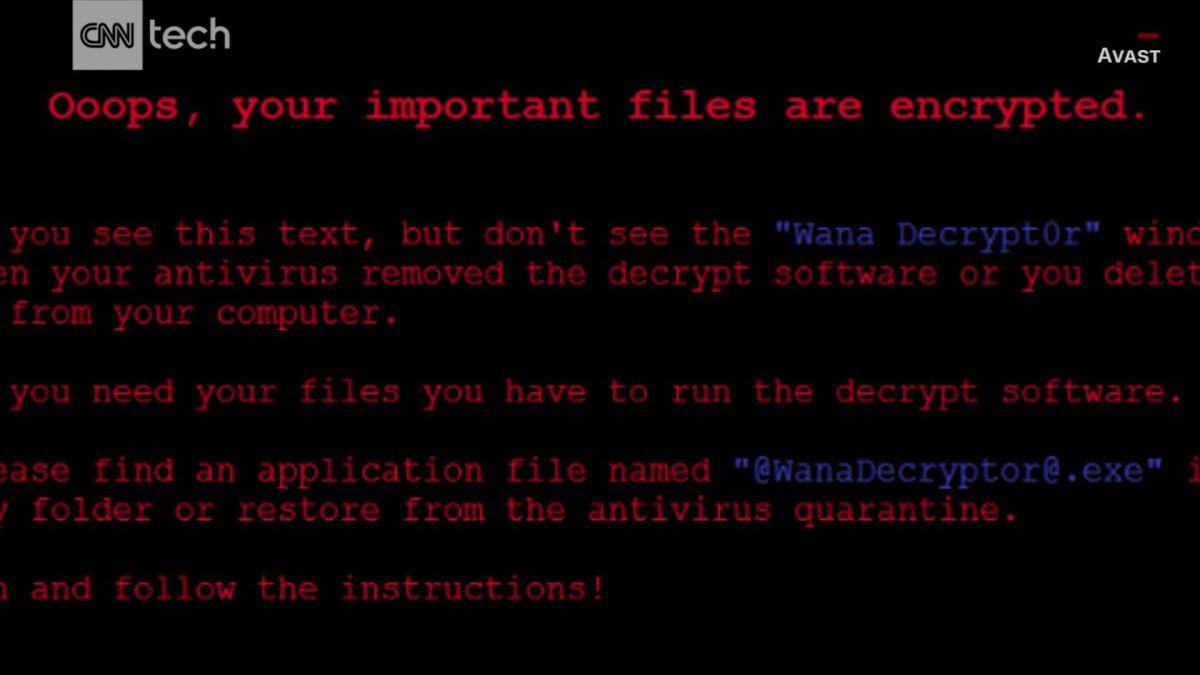
How much do you know about Stuxnet?
Hope Trampski - Sep. 03, 2024
The Stuxnet Worm was discovered in June of 2010 by Sergey Ulasen, an employee of VirusBlokAda, a small antivirus company. At first it was mistaken as an arbitrary Windows bug, just a conflict bet… Read More
-
Eagle Eye: AI and Its Ethical Concerns
Hope Trampski - Aug. 30, 2024
Eagle Eye Eagle Eye, released in 2008, is an action-packed techno-thriller that left audiences clutching their popcorn with anticipation- not because the film was mysterious or nuanced, but beca… Read More
-
Hackers of the 2000s
Hope Trampski - Aug. 27, 2024
If you thought the ‘90s were packed with cybercrime, the next decade brought an even greater wave of cyber threats. The rapid evolution of the internet introduced a multitude of unprecedented cha… Read More
-
Enemy of Realistic Surveillance Depictions
Hope Trampski - Aug. 23, 2024
Enemy of the State, a widely popular political action thriller starring Will Smith is much more than just a gripping nail-biter, it was a look into the realities of modern-day surveillance techni… Read More
-
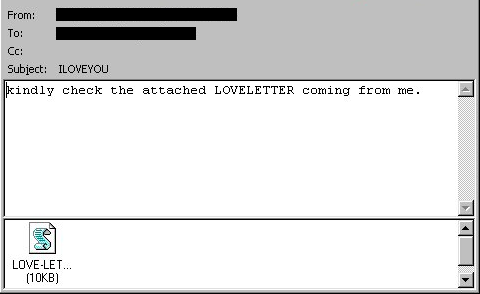
The ILOVEYOU Worm, A Global Crisis
Hope Trampski - Aug. 20, 2024
The ILOVEYOU worm is known as one of the farthest reaching occurrences of malware to date, having affected around 45 million users in only 10 days. The worm caused around $10 billion in damages, … Read More
-
Cyber Unrealism: The Net
Hope Trampski - Aug. 16, 2024
The Net 1995 The 1995 film, The Net, starring Sandra Bullock was one of Hollywood's first attempts at an action-packed cyber thriller. It follows the main character Angela Bennett as she goes on … Read More
-
Hackers of the '90s
Hope Trampski - Aug. 13, 2024
In 1990, the turn of the decade saw a massive uptick in the number of computer hackers as the internet evolved into the tool we know it as today. While the World Wide Web didn’t become available … Read More
-
The Beekeeper, Keeping it Unrealistic
Hope Trampski - Aug. 09, 2024
The Beekeeper, released in January of this year, is an action suspense thriller that stars Jason Statham with a premise around cyber scams. We follow him through a campaign of vengeance as he tri… Read More
-
Porches and Pacific Bell Dumpsters
Hope Trampski - Aug. 06, 2024
In 1990 in Los Angeles, California, Michael B. Peters won a Porsche from the Los Angeles radio station KIIS-FM. Well...not really. Kevin Poulsen is a well-known hacker who took over all the tel… Read More
-
Hackers, a '90s Cautionary Tale
Hope Trampski - Aug. 02, 2024
Hackers, released in 1995, showcased ridiculous visuals and at times an equally ridiculous portrayal of hackers. It is chalked full of ‘90s cyberpunk flair. If this movie could be summed up in on… Read More
-
Viruses of the 80s
Hope Trampski - Jul. 30, 2024
As we discussed in a recent blog post, Creeper is known as the first computer virus. However, the first malicious virus was actually created by a 15-year-old high school student named Rich Skrent… Read More
-
The Matrix, Far From Reality?
Hope Trampski - Jul. 26, 2024
The 1999 film The Matrix was a revisionary movie in plot, special effects, and references to modern technology. It fascinated audiences with action, drama, and high stakes all while keeping to a … Read More
-
Do you know what the Morris worm is?
Hope Trampski - Jul. 23, 2024
In 1988 there was only a meager 60,000 computers connected to the internet. But this low number of the late 80s may have been for the best. On November 2nd, 1988, the Morris worm began to wreak h… Read More
-
War Games and Grim Warnings
Hope Trampski - Jul. 19, 2024
The film War Games, released in 1983, captivated audiences with a thrilling depiction of military super computers and the possibility of nuclear war. Hidden within the story of a young boy with a… Read More
-
Kevin Mitnick, sound familiar?
Hope Trampski - Jul. 16, 2024
Kevin Mitnick is known as one of the world’s first cybercriminals, but before his infamous hacking career, he got his start in social engineering at only twelve years old. Living in Los Angeles, … Read More
-
Sneakers, a 90s Cyber Success
Hope Trampski - Jul. 12, 2024
Here at cyberTAP we value real world applications, and as cyber professionals, we understand the practical nuances of our industry and how it applies to everyday life. However, the same can’t alw… Read More
-
How much do you know about the history of cybersecurity?
Hope Trampski - Jul. 09, 2024
Welcome to our deep dive into the history of cybersecurity! Join us as we uncover the development of our field through the decades by looking into some of the most notorious hacks and cybercrimin… Read More
-
OK, I know what Zero Trust means. Now what?
Matthew Crain - Apr. 13, 2022
In the previous article, I spent some time unpacking NIST’s seven tenets of zero trust. However, those ideas only describe what zero trust intends to accomplish, and that leaves many questions un… Read More
-
Let's talk about NIST
Staff Author - Apr. 06, 2022
Since the creation of the TCP/IP protocol in 1983, that created the building blocks of the internet we know and love today, the technological world that we live in is rapidly evolving. Every inno… Read More
-
Amazon Patents Smell and Skin Texture as Biometrics
Chuck Garwood - Mar. 29, 2022
Amazon was recently awarded several patents for using biometrics such as smell and skin texture to identify people. Amazon’s Ring cameras have been a bit of an outlier lately as they don’t offer … Read More
-
Log4j Rehashed
George Bailey - Mar. 22, 2022
It was December 10, 2021, when the cybersecurity community was ablaze with hunting down yet another critical vulnerability. I know it's hard to keep vulnerabilities straight when they are discove… Read More
-
Purdue Cybersecurity Apprenticeship Program is Ready to Enroll
James Stratton - Mar. 09, 2022
Does your company need to upskill your cyber-team? Are you an individual working in a cyber role and want to become a cyber-apprentice? Are you a US citizen? Then get in here and let’s have a cha… Read More
-
Identity Broker: How Does it Fit in the Identity Management Puzzle
Mike Johnson - Feb. 25, 2022
Recently for a project, the need arose to seamlessly, or as seamless as possible, connect two disparate Learning Management Systems so that users from one system can access content from another w… Read More
-
What it SIEMs vs. What it is: Exploring the Commonalities and Differences between SIEM, MSSP, and MDR.
Staff Author - Feb. 15, 2022
Adopting a new technology in the workplace can lead to major changes in policies and/or procedures. Adopting a new security technology is no different; no matter your choice, there will be benefi… Read More
-
Intro to Zero Trust
Matthew Crain - Jan. 27, 2022
This is the first in a planned series of articles about the concept of zero trust. It is a big subject; today, we will start small, and focus on getting the most basic understanding of just what … Read More
-
Salesforce Says, "Yes," To MFA
Staff Author - Jan. 11, 2022
"You know how we tell the good guys from the bad guys? The bad guys shoot at us." Rick Yancey learned this from his father, a concept that can be applied to the cyber world. The "bad guys" are fi… Read More
-
Tor, What Is It Good For
Krassimir Tzvetanov - Jan. 05, 2022
In early December, Radio Free Europe reported that Russia blocked the Tor service. Is that an effort to fight online crime and illegal content, or is there something deeper? Spoiler alert - I won… Read More
-
Cyber Predictions For 2022: What's Coming Next Year
Eric Engle - Dec. 14, 2021
It's December, so you know what that means; it's prediction season! It's the particular time of year when everyone gives their opinion on what will happen next year in cyber. We, of course, are n… Read More
-
What's Your Stripper Name? Social Engineering Through Viral Media
Staff Author - Dec. 07, 2021
Around the time Eminem started asking if he could have our attention, another trend was taking off across the world in the form of Social Media. The rise of social media brought with it a new tec… Read More
-
Everyday Habits That'll Increase Your Cybersecurity
Staff Author - Nov. 30, 2021
Before coming to cybersecurity, many professionals have different ideas and practices than are required to preserve the security of information. These practices often include: clicking on links i… Read More
-
New cybersecurity law providing support for K12
Joe Beckman - Nov. 23, 2021
Distinguished as one of the few pieces of legislation to be signed by the President of the United States in the past decade, Public Law 117-47, known as the K-12 Cybersecurity Act, requires the f… Read More
-
CMMC v2.0 Launched...Well, Sort Of
George Bailey - Nov. 16, 2021
As many readers of the cyberTAP blog already know, suppliers of goods and services to the United States Department of Defense (DoD) have been put on notice to improve their cybersecurity postures… Read More
-
The Passwordless Future
Micah Snabl - Nov. 09, 2021
For a long time in the world of computers, "security" has nigh been synonymous with "passwords". "Make complex passwords." "Don't share your passwords." "A member of our staff will never ask you … Read More
-
Ransomware in Critical Infrastructure, and What You Should Already Be Doing
Matthew Crain - Nov. 02, 2021
Ransomware attacks show no sign of slowing down anytime soon. In late September, one after another, two large ransomware attacks targeting the agriculture industry came to light. The ransomware g… Read More
-
Where is the privacy with wearable technology?
Scott Richards - Nov. 02, 2021
So, when I decided to write about privacy with modern technology, I found an interesting thing occurred. I was convinced that the privacy concerns would break down over age groups. I started rese… Read More
-
Purdue@WestGate hosting Cybersecurity Demo Day in partnership with Purdue cyberTAP and Purdue MEP
Staff Author - Oct. 25, 2021
Tuesday, October 26th, Purdue@WestGate is hosting an all-day, in-person networking event for students, small-business owners, or anyone interested in pursuing a cybersecurity career to network an… Read More
-
Open Source in Application Development: Safe or Total Thermal Nuclear War?
Mike Johnson - Oct. 19, 2021
Are open-source software tools safe to use in application development? Probably...Sometimes...It Depends. Truthfully, it is challenging for a general consumer to know if a developer has knowingly… Read More
-
Cybersecurity Awareness Month: Secure Your Phishing Defenses
Staff Author - Oct. 12, 2021
From ransomware to SolarWinds, the cybersecurity space has been as hectic as it has ever been over the last 12-24 months. However, for all of the emerging threats and news that are cropping up on… Read More
-
Cybersecurity Awareness Month: Get Familiar with the Cyber Basics
Staff Author - Oct. 05, 2021
At a time when we are more connected than ever, being “cyber smart” is of the utmost importance. This year has already seen more than a fair share of attacks and breaches, including the SolarWind… Read More
-
Year in Review - Message from the Director
Mat Trampski - Sep. 28, 2021
Hello again everyone! Thanks for giving cyberTAP your attention; we very much appreciate our partners, clients, and friends. Without you we’d be really bored, not to mention, without you we could… Read More
-
Knock! Knock! Your Package Has Arrived: Amazon's New In-Garage Delivery Service
Chuck Garwood - Sep. 21, 2021
Amazon recently announced a new delivery service, where they will deliver packages directly into your garage. No more worrying about porch pirates stealing your Amazon Prime Glitter Bombs off you… Read More
-
In Ransomware, the Kids Aren’t All right. The Taxpayers aren’t Either.
Joe Beckman - Sep. 04, 2021
According to their website, the Judson Independent School District in Texas discovered on June 17, 2021, that it was victimized by ransomware. The attack made unavailable the district’s critical… Read More
-
Not just a matter of Gbps - Classifying DDoS Attacks
Krassimir Tzvetanov - Aug. 10, 2021
Distributed Denial of Service (DDoS) attacks are becoming prevalent in our daily life. Just in the past ten years, things have changed significantly – from the forgotten hacktivist collective Ano… Read More
-
I Am Not a Cyber Expert - Odds Are, You Aren’t Either.
Staff Author - Aug. 03, 2021
Three years ago, I thought I had everything figured out. Finish up school, land a job doing something in the field I studied in, raise a family, etc. Little did I know my path was going to change… Read More
-
Cybersecurity Insurance - Another tool in your risk management strategy
George Bailey - Jul. 27, 2021
At the core of all cybersecurity policies, procedures, standards, guidelines, frameworks, technical controls, training, etc., is the idea of risk management. Managing the risk of a data breach t… Read More
-
Don't Threaten Me with a Good Time -- DPAs in Modern Business
Staff Author - Jul. 07, 2021
We were a little surprised recently when we received a DPA that included requirements to comply with regulations in Dubai and New Zealand. Dubai? Why a city and not a country? Heck, why not just … Read More
-
Ransomware is a Scourge, But Also Helpful
Matthew Crain - Jun. 29, 2021
Everything, everywhere, eventually comes down to money. Even non-profit health care organizations tend to operate as if they have investors peering over their shoulders, because each dollar repre… Read More
-
Training the Next Cybersecurity Professionals
Staff Author - Jun. 23, 2021
Over the past 18 months, the world has transformed, and many professionals relocated to working in a remote setting. Unfortunately, the speed at which this transition took place, coupled with the… Read More
-
The Colonial Pipeline Attack: A New Phase in Cyber Defense
Joe Beckman - Jun. 15, 2021
Since the initial accusations of election interference in 2016, the steady stream of hacking incidents attributed to the Russian government has plagued US cybersecurity practitioners like chronic… Read More
-
Stopping DDoS in its Tracks
Krassimir Tzvetanov - Jun. 08, 2021
I often get asked, "What’s the best equipment one can buy to protect my company from a Distributed Denial of Service (DDoS) attack?" While this is a valid question it is making a very large numbe… Read More
-
Message from the Director - June Update
Mat Trampski - Jun. 01, 2021
The very excellent Eric, with whom rests the primary responsibility of our blog and newsletter, has been badgering me for some time to provide a note from the director. He’s been patient and I’ve… Read More
-
The Critical Security Controls for Small to Medium Size Business.
Nate Bradbury - May. 18, 2021
The Center for Internet Security (CIS) is a non-profit organization dedicated to developing guidelines and standards to help organizations and individuals alike protect themselves from internet t… Read More
-
Don't Trust Users: Application Security Basics
Micah Snabl - May. 11, 2021
When it comes to application security, it pays to be a cynic. When developing a tool, it is quite easy to focus on all of the things it is supposed to accomplish. The converse is of similar impor… Read More
-
Phishing: Beware of those Sneaky, Slimy, Stinky Messages
George Bailey - May. 04, 2021
It’s 3 am, you are abruptly awoken from a deep sleep by a banging on your door. You wipe the sleep from your eyes and glare at your alarm clock, who could that be at this hour, you say to yourse… Read More
-
Securing Mr. Roboto: Cybersecurity in ICS Environments
Joe Beckman - Apr. 27, 2021
The February 5, 2021 attack on the Oldsmar, Florida water supply brought the cybersecurity of industrial control systems (ICS) to the front of national attention in the United States. As is often… Read More
-
A Letter to Cybersecurity from an Application Developer
Mike Johnson - Apr. 20, 2021
Dear Cybersecurity, I don't get you. I thought we were going to be good friends instead, you hang out with all my other friends. You've changed, I don't recognize you anymore. I know we haven't a… Read More
-
What is Cyber Threat Intelligence?
Staff Author - Apr. 13, 2021
Over the past 8-10 years, the term Cyber Threat Intelligence (CTI) permanently settled in our dictionary. But what is it? Apart from every term containing "cyber" is cool, it does not appear we h… Read More
-
What it Takes to Admin SaaS
Staff Author - Apr. 06, 2021
What does it take to administer a SaaS (Software as a Service) application? Well, here are some thoughts. First, you need to know what the software can do. I don't mean the stuff they put on the … Read More
-
What is CMMC?
George Bailey - Mar. 30, 2021
Wait, What, another cybersecurity standard to implement?!? Yes, amongst all the available choices from NIST, FIPS, ISO, COBIT, ISACA, PCI, and many others, a new standard has been developed. This… Read More
-
Defense Lives Here: What a former B1G Ten Defensive Player of the Year can teach us about defensive cybersecurity?
Mat Trampski - Mar. 16, 2021
In 2015 Purdue University’s perimeter was secure. The necessary controls in place demonstrated to our most sophisticated adversaries that nothing would be “easy” from the outside. To match this s… Read More
-
Moving a Workforce Out Of Office
Mike Johnson - Mar. 09, 2021
Raise your hand if the current pandemic climate has accelerated a change or outright shift in the way you do business. Keep your hand raised if you weren’t 100% prepared for this shift. For those… Read More
-
Why Do I Need a Cybersecurity Risk Assessment?
Matthew Crain - Mar. 02, 2021
Every cybersecurity program I’ve ever seen lists risk assessment as its first step, a foundation upon which all the other security measures will build. But with so many potential fires to fight, … Read More
-
Understanding the SolarWinds “Sunburst” Hack
Joe Beckman - Feb. 23, 2021
You could be forgiven if you rolled your eyes and clicked through to the next story when you first learned of the SolarWinds hack. Cybersecurity incidents have become commonplace events and if yo… Read More
-
Knowledge is Power
Staff Author - Feb. 16, 2021
Picture if you will a special operative who has been given the directive of establishing communication between generals on the field of battle. These generals are from different countries and spe… Read More
-
Welcome to the cyberTAP
Mat Trampski - Feb. 09, 2021
I’m a lucky guy, what else can I say! Good health, good family, and a good job… The world faces the shifting sands of an ever-changing cybersecurity landscape: new strains of ransomware popping u… Read More