Cybersecurity Insurance - Another tool in your risk management strategy
At the core of all cybersecurity policies, procedures, standards, guidelines, frameworks, technical controls, training, etc., is the idea of risk management. Managing the risk of a data breach to an acceptable level is no easy task. Generically speaking, risk management is the process of determining an acceptable level of risk, calculating the current level of risk, and then either accepting the level of risk or taking steps to reduce the acceptable level of risk via mitigation or transference. Risk mitigations might include adding technology to help secure the network, or it could be instituting a new policy to protect a critical business process. Whatever the mitigation is, it generally requires a change of some kind to be implemented.
Cybersecurity insurance is designed to transfer losses from a variety of cyber incidents, including data breaches, business interruption, and network damage. A robust cybersecurity insurance partner could help an organization with recovering from several types of successful cyber-attacks by: (1) promoting the adoption of preventative measures in return for more coverage; and (2) encouraging the implementation of best practices by basing premiums on an insured’s level of self-protection; (3) by providing hands-on, reactive services when a breach or compromise is detected.
In the last 5 years, many organizations would have had to close their doors if they didn’t have a cybersecurity insurance policy that they could lean on for help. Why? Ransomware! Ransomware is a type of cyber-attack where the bad actor encrypts (e.g., Locks up) an organization’s data and demands the payment of a ransom to receive the key to unlock the data. Ransomware uses very strong encryption; in many cases, the same type of encryption organizations implements to safely protect their data from prying eyes. Without the key, the probability of recovering encrypted data is minuscule if a robust backup strategy is not in place. I am not going to debate in this blog if ransoms should be paid or not, happy to do so if you like, send me an email or at me in a tweet.
The surge of successful ransomware attacks in the last two years has caused the cyber insurance industry to take it on the chin. In many cases cyber insurance coverage was used to purchase bitcoin (an electronic currency) to pay the ransom, in cases where the ransom was not paid, insurance coverage was used to finance an aggressive response to the attack by performing data restoration and recovering systems, networks, and data to a pre-attack state. In a few documented cases, the cost of recovery supported by cyber insurance was more than what was demanded as a ransom. Keep in mind that it is believed that 40% of victims that paid the demanded ransom were still unable to recover their data once keys were obtained.
Do I recommend cyber insurance as part of an organization’s risk management strategy? Absolutely! Traditional commercial general liability and property insurance policies typically exclude cyber risks from their terms, leading to the emergence of cybersecurity insurance as a “stand alone” line of coverage. That coverage provides protection against a wide range of cyber incident losses that businesses may suffer directly or cause to others, including costs arising from data destruction and/or theft, extortion demands, hacking, denial of service attacks, crisis management activity related to data breaches, and legal claims for defamation, fraud, and privacy violations. Few cybersecurity insurance policies, however, provide businesses with coverage for an area of growing private and public concern: the physical damage and bodily harm that could result from a successful cyber-attack. This could be very concerning for the healthcare industry where a Denial-of-Service attack or a medical device hack could lead to the death of a patient.
Keep in mind that that with insurance coverage, not all cyber-attacks may be covered by your policy. It is highly advised that the terms and conditions of your policy is communicated across all organizational leadership. Although, it might be the finance department that owns the policy; the information technology department and security official (if you have one) needs to be fully aware of the finer points of the policy. Why? Some policies will stipulate that you must report cyber incidents to your insurance company, even if a claim is not opened. If a major breach occurs, and it is discovered that it could have been prevented by addressing a smaller, “just noise” type of incident, and that incident was not reported, your claim could be denied. I have seen many IT leaders that don’t know if their company has coverage let alone seen the policy requirements; don’t be that organization. This is more a dilemma with larger organizations, if regardless of your size be sure your IT support (whoever that may be) is aware that someone from your organization needs to understand the details of all cybersecurity incidents they help to resolve.
George, how much coverage should my organization purchase? That’s a good question, and it is highly variable to the type of business you operate, the industry vertical you’re in, the volume of data you retain, and your current cybersecurity posture. Keep in mind that like any risk reduction technique, you must perform a bit of a cost-benefit analysis when purchasing cyber insurance. I like to keep the Ponemon Institute’s Cost of a Data Breach report in mind when thinking about how much breaches can cost an organization. The current report analyzed global data breaches from August 2019 through April 2020 from 524 organizations. The average cost of a data breach was $3.86 million dollars. Ouch, I know! Costs have declined by 1.5% since the last reporting period. The average cost per record for a PII (personally identifiable information) breach is $150. If you are a small-medium-sized business, you could take the number of PII records you retain and multiply it by $150; this in my opinion would be the absolute lowest coverage level you would purchase. Keep in mind that this is an average cost, and some organizations will experience much higher recovery costs.
Those seeking a new cyber insurance policy may unexpectedly find that their organization is not insurable. Due to the high costs that the insurance industry has suffered between 2019 – 2021 insurance underwriters are increasing the minimum cybersecurity requirements that policyholders must implement. Organizations seeking to renew or increase their coverage will be subject to similar requirements. Whether you are seeking coverage or will be renewing soon, all organizations should be ready to pay higher premiums, and higher retention (e.g., deductibles) to purchase coverage. cyberTAP would be delighted to help your business understand what your risks are and determine an appropriate level of cyber coverage.
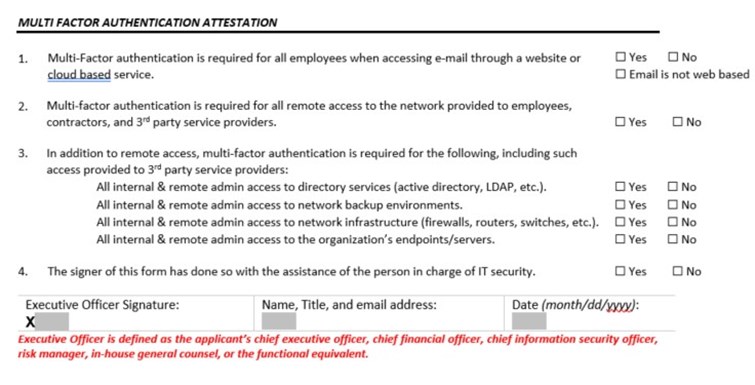
Here are examples of questionnaires and attestation statements organizations will have to complete when applying for cyber insurance. The maturity of your cyber program will need to increase as the amount of coverage goes up.
Example #1:

Multi-Factor Authentication
Multi-factor authentication refers to the use of two or more means of identification and access control—sometimes referred to as “something you know, something you have, or something you are.” A username and password, for example, is something you know. Requiring a code sent via text message (SMS) establishes “something you have,” i.e., a mobile phone belonging to you. Biometric authentication, through a fingerprint or retina scan, establishes “something you are.” Multi-factor authentication is successfully enabled when at least two of these categories of identification are required in order to successfully verify a user’s identity when accessing systems.
Multi-Factor Authentication for Remote Network Access
Requiring multi-factor authentication for remote network access is an important security control that can help reduce the potential for a network compromise caused by lost or stolen passwords. Without this control, an intruder can gain access to an insured’s network in a similar manner to an authorized user.
Multi-Factor Authentication for Administrative Access
Requiring multi-factor authentication for both remote and internal access to administrative accounts helps to prevent intruders that have compromised an internal system from elevating privileges and obtaining broader access to a compromised network. The existence of this control can prevent an intruder from gaining the level of access necessary to successfully deploy ransomware across the network.
Multi-Factor Authentication for Remote Access to Email
Requiring multi-factor authentication for remote access to email can help reduce the potential for a compromise to corporate email accounts caused by lost or stolen passwords. Without this control, an intruder can easily gain access to a user’s corporate email account. Threat actors often use this access to perpetrate various cyber crime schemes against the impacted organization and its clients and customers.
The controls described above and listed below are the minimum controls that must be in place in order to be eligible for a CyberRisk policy. Because of the importance of the controls in preventing ransomware attacks the following attestation should be completed with the assistance of the person(s) in charge of network security. If network security is outsourced to a managed security provider or other 3rd party please complete the attestation below with their assistance.
Multi-Factor Authentication Attestation
During this age of surging cyber-attacks, cybersecurity insurance is a valuable resource to have in your risk management tool chest. Just like any other cybersecurity control, cyber insurance is not a silver bullet. It will not prevent a compromise; however, it can provide almost immediate assistance if you experience a breach that stretches your internal capabilities beyond their breaking point. If you need help determining what type of coverage you need, or reviewing your current policy Purdue cyberTAP can help.




