Cybersecurity Awareness Articles
-
Haunted Networks & Ghosts in Machines: Cybersecurity’s Spooky Side
Hope Trampski - Oct. 31, 2025
Even when we think that viruses are gone, worms have been eliminated, and cybercriminals taken care of, traces can still linger. Just because we can’t see them, doesn’t mean they are gone for goo… Read More
-
Quick Guide: Cybersecurity for College Students
Hope Trampski - Oct. 30, 2025
Continuing with our quick guide series, today we’ll be going through some smart habits and safety tips for current college students. While this is aimed at college students living and working on … Read More
-
Quick Guide: Cybersecurity for Teens
Hope Trampski - Oct. 21, 2025
Today's teens are more connected to the digital world than ever before. They aren’t just on social media; they’re online gaming, shopping, and messaging. Even if your teen isn’t on social media, … Read More
-
Quick Guide: Cybersecurity for Execs
Hope Trampski - Oct. 14, 2025
Executives today take on a lot. They spearhead their organization and often lead their industry on a massive scale. Unfortunately, this makes them primary targets for cybercriminals. Essentially,… Read More
-
Quick Guide: Cybersecurity For Seniors
Hope Trampski - Oct. 07, 2025
Cybersecurity matters at every age. Older generations are currently facing a multitude of challenges in this new age of technology. The adjustments that they need to make to participate in an onl… Read More
-
Quick Guide: Cybersecurity for Kids
Hope Trampski - Oct. 01, 2025
Kids today are born into a fully digital world; they won’t know a life without the modern-day conveniences of technology. From tablets, to TV, to phones, kids have access to just about anything y… Read More
-
The Business Impact of a Breach: What Every Exec Needs to Know Before the Headlines Hit
Hope Trampski - May. 13, 2025
It's not if, but when. Data breaches happen daily, and the reality is that one might be closer to your organization than you may think. Every executive should be taking the proper steps to prepar… Read More
-
Newest HIPAA Rules
Hope Trampski - Apr. 24, 2025
What is HIPAA & What Does it Have to do with Me? Before we take a look at the new proposed HIPAA rules, let's cover what HIPAA actually is. The well-known acronym stands for Health Insurance… Read More
-
What Do You Mean New CMMC Updates?
Hope Trampski - Apr. 10, 2025
Prior to the beginning of this year the Department of Defense released a new set of Cybersecurity Maturity Model Certification (CMMC) guidelines. So, what is the CMMC? The CMMC program is a wa… Read More
-
Women in Cyber Today
Hope Trampski - Mar. 27, 2025
Thanks to the accomplishments of the pioneers before them, today’s women in cybersecurity are making leaps and bounds toward a more secure future. Let’s take a look at some of the most influentia… Read More
-
Women in Cyber: The 80s Era
Hope Trampski - Mar. 13, 2025
Today’s focus will be on the 80s era of computer science, a pivotal time for our field. The decade seemed to bring discoveries daily with the blossoming internet and the development of new progra… Read More
-
Women In Cyber: The NASA Years
Hope Trampski - Mar. 12, 2025
NASA is known as one of the greatest pioneers in the pursuit of knowledge in our modern era. Over and over, we hear about their success in the exploration of space and their advancements in the f… Read More
-
Women In Cyber: The Beginnings
Hope Trampski - Mar. 04, 2025
Ada Lovelace Ada Lovelace was a mathematician and writer in the early 1800s, best known for her work on the Analytical Engine. During her career she worked with Charles Babbage, who developed t… Read More
-
Hacktivism: Scambaiting
Hope Trampski - Jan. 12, 2025
To close out our series on hacktivism, we delve into the world of scambaiting, an online practice where internet vigilantes attempt to turn the tables on hackers and protect potential victims. Th… Read More
-
Hacktivism: Anonymous
Hope Trampski - Dec. 19, 2024
Origin The hacktivist group Anonymous was founded in 2003 on an imageboard, 4chan, which was a forum where users could anonymously post images and discussions. The name Anonymous originated from… Read More
-
Hacktivism: DarkSide Hacking Group
Hope Trampski - Dec. 12, 2024
DarkSide is a hacking group believed to be based out of Russia. They provide ransomware as a service accompanying their frequent high-profile attacks. First spotted in 2020, the group is fairly … Read More
-
Hacktivism: The Short Life of LulzSec
Hope Trampski - Dec. 05, 2024
Origins LulzSec came onto the scene in 2011 after their first recorded hack against Fox.com's website. ‘Lulz’ stands for laughs while ‘sec’ is shorthand for security essentially meaning every ti… Read More
-
Hacktivism: WikiLeaks
Hope Trampski - Nov. 28, 2024
WikiLeaks is a nonprofit media organization founded in 2006 by Julian Assange, Kristinn Hrdnsson, and Danial Mathews. The site is used to publish leaked documents from governments, corporations, … Read More
-
Hacktivism: The Chaos Computer Club
Hope Trampski - Nov. 21, 2024
Hacktivism: The Chaos Computer Club The Chaos Computer Club, founded in 1981, is Europe’s largest association of hackers. As an organization they stand for ‘freedom of information’ and aim to p… Read More
-
Hacktivism: The Cult of the Dead Cow
Hope Trampski - Nov. 14, 2024
What is the Cult of the Dead Cow? The Cult of the Dead Cow, founded in 1984, started as a group of like-minded hackers looking to improve their skills. As the group developed, they pivoted towar… Read More
-
What is Hacktivism?
Hope Trampski - Nov. 07, 2024
The term hacktivism has been a bit of a buzz word for the past couple of decades, falling in and out of popularity in accordance with the number of politically motivated hacks that grab media att… Read More
-
The Ashley Madison Hack
Hope Trampski - Nov. 01, 2024
Hacking almost always results in the release of personal information. Whether that be credit card numbers, social security numbers, or other sensitive data, leaks happen all the time. In the case… Read More
-
AI As A Tool
Hope Trampski - Oct. 28, 2024
What AI Looks Like Day to Day AI is an ever-evolving field, it seems that every day there is something new in the works. The topic of AI can get pretty complicated pretty quickly. So, realistica… Read More
-
The Dennis Kucinich CBS News Hack
Hope Trampski - Oct. 25, 2024
Hacking, in most cases, is a very selfish act. Most hackers are in it for the money or the information they can turn into money. But in some cases, hackers commit cybercrime because they believe … Read More
-
How Not to Take the Bait When it Comes to Phishing
Hope Trampski - Oct. 21, 2024
Phishing is one of the most common forms of cybercrime, with around 3.4 billion phishing emails sent each day it is nearly impossible to avoid. The good news is that falling victim to these scams… Read More
-
The Triton Malware Attack
Hope Trampski - Oct. 18, 2024
Completely unsolved cybercrime cases are relatively rare. Normally when an attack ensues, one of the most important proceedings is to trace it back to the attacker. This is especially important w… Read More
-
Why Are Software Updates So Important?
Hope Trampski - Oct. 14, 2024
The importance of keeping your software up to date cannot be stressed enough. Often, we find ourselves putting off these updates because it can be inconvenient to be without our devices for the p… Read More
-
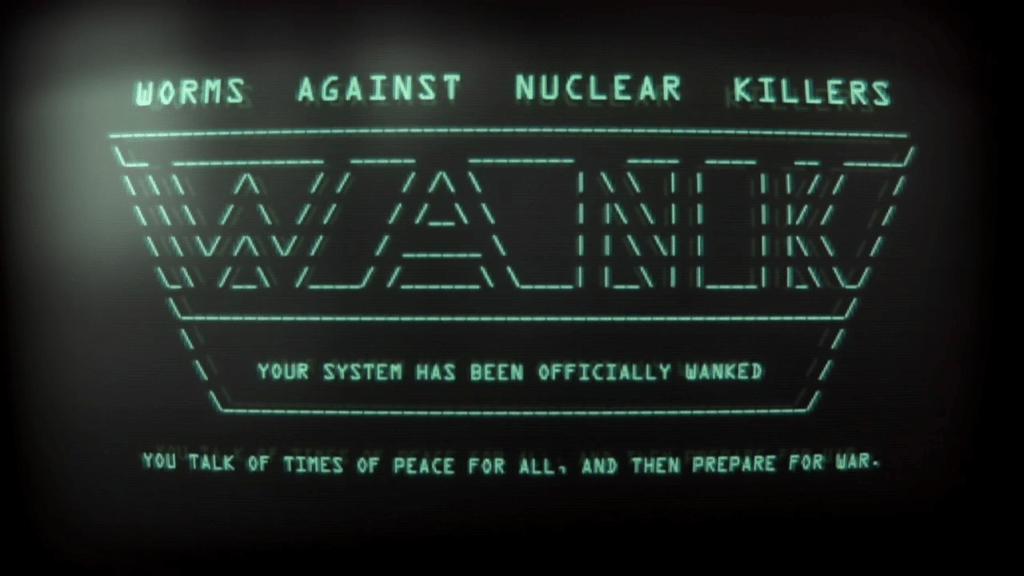
The Mystery of the WANK Worm
Hope Trampski - Oct. 11, 2024
In 1989, Galileo, a nuclear-powered spacecraft created by NASA, was set to launch. Its existence was controversial having been announced in the wake of the Challenger Disaster, but that wasn’t th… Read More
-
Multi-Factor Authentication
Hope Trampski - Oct. 07, 2024
To expand on our discussion about secure passwords from last week, let’s look at multi-factor authentication. Multifactor has only been around for about twenty years, but that's a good chunk of t… Read More
-
Broadcasting Masks and Mayhem
Hope Trampski - Oct. 04, 2024
Welcome to spooky season, we are so glad you could join us for our October series on unsolved cybercrimes! While it might be comforting to think we know the origin of every instance of malicious … Read More
-
Password Security and Password Managers
Hope Trampski - Oct. 02, 2024
Ensuring proper password safety is a never-ending task, mostly because the rules seem to keep changing. The rules used to seem easy; create a password you’ll remember. Oh wait, that’s too easy, t… Read More
-
Where are we now?
Hope Trampski - Sep. 17, 2024
Even after decades of development in our field, one thing stays consistent, change. There are always new threats, new vulnerabilities, new fixes. The only thing that stays the same is that things… Read More
-
How much do you know about Stuxnet?
Hope Trampski - Sep. 03, 2024
The Stuxnet Worm was discovered in June of 2010 by Sergey Ulasen, an employee of VirusBlokAda, a small antivirus company. At first it was mistaken as an arbitrary Windows bug, just a conflict bet… Read More
-
Eagle Eye: AI and Its Ethical Concerns
Hope Trampski - Aug. 30, 2024
Eagle Eye Eagle Eye, released in 2008, is an action-packed techno-thriller that left audiences clutching their popcorn with anticipation- not because the film was mysterious or nuanced, but beca… Read More
-
Hackers of the 2000s
Hope Trampski - Aug. 27, 2024
If you thought the ‘90s were packed with cybercrime, the next decade brought an even greater wave of cyber threats. The rapid evolution of the internet introduced a multitude of unprecedented cha… Read More
-
Enemy of Realistic Surveillance Depictions
Hope Trampski - Aug. 23, 2024
Enemy of the State, a widely popular political action thriller starring Will Smith is much more than just a gripping nail-biter, it was a look into the realities of modern-day surveillance techni… Read More
-
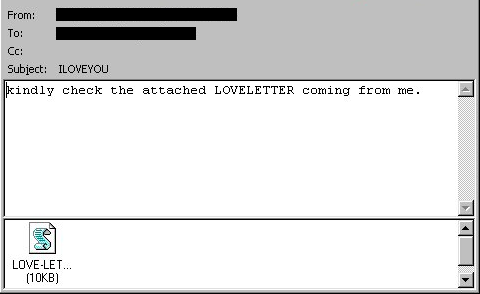
The ILOVEYOU Worm, A Global Crisis
Hope Trampski - Aug. 20, 2024
The ILOVEYOU worm is known as one of the farthest reaching occurrences of malware to date, having affected around 45 million users in only 10 days. The worm caused around $10 billion in damages, … Read More
-
Cyber Unrealism: The Net
Hope Trampski - Aug. 16, 2024
The Net 1995 The 1995 film, The Net, starring Sandra Bullock was one of Hollywood's first attempts at an action-packed cyber thriller. It follows the main character Angela Bennett as she goes on … Read More
-
Hackers of the '90s
Hope Trampski - Aug. 13, 2024
In 1990, the turn of the decade saw a massive uptick in the number of computer hackers as the internet evolved into the tool we know it as today. While the World Wide Web didn’t become available … Read More
-
The Beekeeper, Keeping it Unrealistic
Hope Trampski - Aug. 09, 2024
The Beekeeper, released in January of this year, is an action suspense thriller that stars Jason Statham with a premise around cyber scams. We follow him through a campaign of vengeance as he tri… Read More
-
Porches and Pacific Bell Dumpsters
Hope Trampski - Aug. 06, 2024
In 1990 in Los Angeles, California, Michael B. Peters won a Porsche from the Los Angeles radio station KIIS-FM. Well...not really. Kevin Poulsen is a well-known hacker who took over all the tel… Read More
-
Hackers, a '90s Cautionary Tale
Hope Trampski - Aug. 02, 2024
Hackers, released in 1995, showcased ridiculous visuals and at times an equally ridiculous portrayal of hackers. It is chalked full of ‘90s cyberpunk flair. If this movie could be summed up in on… Read More
-
Viruses of the 80s
Hope Trampski - Jul. 30, 2024
As we discussed in a recent blog post, Creeper is known as the first computer virus. However, the first malicious virus was actually created by a 15-year-old high school student named Rich Skrent… Read More
-
The Matrix, Far From Reality?
Hope Trampski - Jul. 26, 2024
The 1999 film The Matrix was a revisionary movie in plot, special effects, and references to modern technology. It fascinated audiences with action, drama, and high stakes all while keeping to a … Read More
-
Do you know what the Morris worm is?
Hope Trampski - Jul. 23, 2024
In 1988 there was only a meager 60,000 computers connected to the internet. But this low number of the late 80s may have been for the best. On November 2nd, 1988, the Morris worm began to wreak h… Read More
-
War Games and Grim Warnings
Hope Trampski - Jul. 19, 2024
The film War Games, released in 1983, captivated audiences with a thrilling depiction of military super computers and the possibility of nuclear war. Hidden within the story of a young boy with a… Read More
-
Kevin Mitnick, sound familiar?
Hope Trampski - Jul. 16, 2024
Kevin Mitnick is known as one of the world’s first cybercriminals, but before his infamous hacking career, he got his start in social engineering at only twelve years old. Living in Los Angeles, … Read More
-
Sneakers, a 90s Cyber Success
Hope Trampski - Jul. 12, 2024
Here at cyberTAP we value real world applications, and as cyber professionals, we understand the practical nuances of our industry and how it applies to everyday life. However, the same can’t alw… Read More
-
How much do you know about the history of cybersecurity?
Hope Trampski - Jul. 09, 2024
Welcome to our deep dive into the history of cybersecurity! Join us as we uncover the development of our field through the decades by looking into some of the most notorious hacks and cybercrimin… Read More
-
Everyday Habits That'll Increase Your Cybersecurity
Staff Author - Nov. 30, 2021
Before coming to cybersecurity, many professionals have different ideas and practices than are required to preserve the security of information. These practices often include: clicking on links i… Read More
-
Cybersecurity Awareness Month: Secure Your Phishing Defenses
Staff Author - Oct. 12, 2021
From ransomware to SolarWinds, the cybersecurity space has been as hectic as it has ever been over the last 12-24 months. However, for all of the emerging threats and news that are cropping up on… Read More
-
Cybersecurity Awareness Month: Get Familiar with the Cyber Basics
Staff Author - Oct. 05, 2021
At a time when we are more connected than ever, being “cyber smart” is of the utmost importance. This year has already seen more than a fair share of attacks and breaches, including the SolarWind… Read More